| tranquileye > contextualizing the internet, 1995 > social history of the early Internet | | search |
The Internet - the global democratic electronic communication network... Making available a “real-time” library without walls, with electronic messaging, to millions, and in the future billions. While the global transport network provides the backbone for communications, the Internet has created the electronic community among 15 million people (today) and in the future possibly billions. What separates the Internet from a basic transport network are its resources and wide scale public access to information sources. Additionally its co-operative nature (controlled by a democratic committee of multinational origin) and critical support for the academic and government infrastructure of many nations (from the United States to Russia), make it a technological wonder of major social proportions.- Michael Kleeman,
quoted in The Pocket Guide to the Electronic Frontier
|
December
1994 ~ There is a tendency in popular discourse about the Internet, such
as Michael Kleeman’s statement above, to fall into hyperbole and superficial
analysis. In the burgeoning Internet “how-to” book market such descriptions
abound, passed off as some brief measure of uncritical history. Yet there is
a certain attraction to these words; in his short description, one can hear
Kleeman’s sense of wonder, perhaps reflecting the amazement we have felt
upon receiving electronic mail from a friend far away, or at logging onto an
engaging site half a world away. And we begin to wonder, as the noise from the
Information Superhighway becomes louder, just what it is with which we will
be dealing.
Beyond such generalizations as Kleeman’s, however, one finds, for the most part, an easy abundance of technical notes describing an alphabet soup of network protocols and computer operating systems, clean detailed maps of interconnected networks, and page after page of statistics. It is not so much that such material is itself incomprehensible, but rather that it is so difficult to determine the underlying nature of what it describes.
So much of this information, popular and technical both, tends to “abstract technology from society,” as Raymond Williams would say, placing the development of telemetrics in a sphere isolated from the surrounding culture (13). Instead of falling into such a discourse of technological determinism, I will attempt to place the creation of what we now call the Internet into something of a social and cultural context, approaching it not as an evolution toward a ubiquitous service, but rather as a series of needs, innovations, and results. In this effort I am inspired to some extent by Williams and by Michel Foucault, who in an interview said the following about the innovation of placing the chimney inside the medieval European home:
Why did people struggle to find the way to put a chimney inside a house? Or did they put their techniques to this use? So often in the history of techniques it takes years or even centuries to implement them. It is certain, and of capital importance, that this technique was a formative influence on new human relations, but it is impossible to think that it would have been developed and adapted had there not been in play and strategy of human relations something which tended in that direction. What is interesting is always interconnection, not primacy of this over that, which never has any meaning. (169)
It is this interconnection which I would suggest is key to studying the development of the Internet, or any other seemingly complex and apparently baffling communications structure.
Obviously, my effort to create a history of the Internet must be, by its nature, incomplete, as the network continues to change and grow; the seminal history of the matrix, which I hope will create a more detailed framework for analysis of the network, has yet to be written. Rather, I will venture to create a starting point for a more critical analysis of the development of internetworking technologies, and the social dynamics therefore created. I will do this by identifying what I consider to be a set of processes which have characterized the Internet’s development, and which continue to distinguish it today: a set of dynamics, as Foucault might say, between ideals and practices.
The individual encounter with the fluid environment created by technology, what Appadurai calls the technoscape, is one of the principle narratives of post-modern culture, and possibly the prime narrative of the Internet itself. This encounter has taken many forms, and had many results; what I wish to highlight is the unique relationship which can exist between an inquisitive individual and a computer in the second half of the 20th century, a process which, for the past thirty years, has been called “hacking.” It is a relationship which can best be compared, I think, to the encounter of the Enlightenment scientist with nature, an engaging process of exploration, experimentation, and manipulation.
The term hacking became synonymous in the 1980s with the circumvention of computer security systems, but in fact has its origins at the Massachusetts Institute of Technology, were hacking was defined as a particularly elaborate, quasi-technological prank (Levy 23). During the 1950s, the term began to be used by the members of the MIT Tech Model Railroad Club to describe modifications and improvements to their complex train set-up; eventually, the word made its way to the activities of MIT students who experimented with the five million dollar TX-O mainframe computer in the early-1960s (23).
The story of the former model railroaders creating small programs on the TX-O is the core narrative of Steven Levy’s Hackers: Heroes of the Computer Revolution; it is one of technology being encountered, studied, understood, and then manipulated to create a desired result. Levy identifies what he calls a “hacker ethic,” a set of principles which both defined and guided the hacking community. Writes Levy:
The precepts of this revolutionary Hacker Ethic were not so much debated and discussed as silently agreed upon. No manifestos were issued. No missionaries tried to gather converts. The computer did the converting, and those who seemed to follow the Hacker Ethic most faithfully were people ... whose lives before MIT seemed to be mere preludes to that moment when they fulfilled themselves behind the console of the TX-O. (39)
Levy goes on to specify the characteristics of this culture, which were central to the computer hobbyist community and to the development of the personal computer industry well into the 1980s. Writes Levy:
Access to computers - and anything which might teach you something about the way the world works - should be unlimited and total.... All information should be free... Mistrust authority - promote decentralization... Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race, or position... You can create art and beauty on a computer... Computers can change your life for the better. (39-45)
It was during the years of the anti-war movement in the late-1960s at MIT that another aspect of the hacker mentality came to the fore. By then, computer research had grown into a huge enterprise at many universities, often with the direct financial support of the U.S. Department of Defense. Many hackers believed they could rationalize the source of their funding, and still remain true to their ideals of free flow of information and co-operative anarchy. Regardless of such protestations, however, when the MIT Artificial Intelligence lab was threatened by possible anti-war protests in 1968, the lab manager had elaborate security systems installed, with clear restrictions on who could access the lab (Levy 131-132). I do not want to make too much of such incidents; some computer facilities were, in fact, attacked and damaged. But it illustrates what can be seen as the limit to the effectiveness of the hacker ethic. Levy quotes MIT hacker Tom Knight: “There was a set of shared goals, a set of shared intellectual excitement, even to a large degree a set of shared social life, but there was also a boundary which people were nervous to go beyond” (134).
Levy writes of a hacker community which held certain ideals, but which was also inward-looking and insular. This community would, for more than twenty years, define the technology of the Internet. From this encounter of individual with computer, we will now turn to the encounter of culture with institution.
It is the process of mediation between the hacker culture and various government and military institutions which provides the second substantive narrative of the development of the Internet. It has become something of a cliché in popular discourses of the Internet to speak of it as anarchistic, decentralized, and democratic. I would contend that is more accurate and useful to speak of the dynamic between such tendencies and opposing desires for control and centralization. I would suggest that such centralizing tendencies are best embodied in the form of the institutions which have, for twenty-five years, provided substantial financial support for the creation of first ARPANet and later Internet. In the 1990s, these institutions are primarily commercial; in the 1980s, education and research-oriented; and in the 1960s and 70s, military.
It was the U.S. Defense Department Advanced Research Projects Agency (ARPA) which supported the creation of the Internet in the 1960s and 70s, and was responsible for much of the network’s growth in that period. ARPA was created in the 1950s, in part in response to perceived inadequacies in American military research and development programs (Zitner A-96). Managed to a great extent by computer scientists, including ARPANet program director Larry Roberts, the agency had been supporting research into possible military applications of computer technology since its inception (Crocker; Levy 131). ARPA’s approach to such research was to fund widely with the expectation that independent research at a variety of sites would yield results useful to the military in future. ARPA funded research at MIT on artificial intelligence, and in 1967 distributed a proposal for a new computer network which would link four ARPA research sites (Levy 131; Hauben).
There is some disagreement concerning the motivation for ARPA’s funding of research into computer networking in the 1960s. The majority view, held by Hardy and most of the popular press, is that ARPA was interested in creating a large, robust military communications network which could survive a nuclear attack (Hardy, Cerf and others). Quarterman and Zitner suggest that the goal was somewhat more sanguine; ARPA-supported researchers at different sites each required access to a high level of computer technology, requiring ARPA to purchase a new machine for each site (Quarterman 37). Networking the sites together would allow researchers to log into other computer facilities, and thus save money.
Regardless, the networking technology which ARPA chose to promote was significant. The convention in computer networking in this period was circuit-switching, client/server set-ups; one computer would act as the central hub which would control the flow and content of information on the network (Comer, Internetworking 56). ARPA funded the development of a different technology called packet switching, which creates a host/host relationship among networked computers. In essence, each computer on a packet network acts as both server and client. Data is broken down into small units called packets or datagrams, each of which contains the information itself and data as to the packet’s final destination. If any message is too large for one datagram, the packet switching technology will split it up into several datagrams, and insure that they all arrive correctly. Packets are routed by each computer in the network, creating a more decentralized method of handling data, and allowing a variety of originators to use the same communications line (Hedrick).
By 1968, ARPA computer researcher Larry Roberts had sketched out the design of the network, and bids were taken to supply the special Interface Message Processors (IMP) which would connect each site to the network. IBM, stating that the planned network was impossible to build and would not function, refused to bid (Hafner 153). The first network would connect four primary ARPA research sites: the University of California at Los Angles, Stanford University, University of California at Santa Barbara, and University of Utah. With the goal of having the network operational on Labour Day, 1969, ARPA left the actual design of the interface and much of the networking protocols up to the contractors who had built the IMPs, and to a group of hackers, mostly students, representing each site.
Writes Stephen Croker, then a graduate student at UCLA and a project participant:
Over the spring and summer of 1969 we grappled with the detailed problems of protocol design. Although we had a vision of the vast potential for intercomputer communication, designing usable protocols was another matter. A custom hardware interface and custom intrusion into the operating system was going to be required for anything we designed, and we anticipated serious difficulty at each of the sites. We looked for existing abstractions to use. It would have been convenient if we could have made the network simply look like a tape drive to each host, but we knew that wouldn't do. (“RFC 1000”)
ARPANet went online on Labor Day, 1969.
The ARPANet of the late-1960s and early-1970s was quite different from the Internet of today. It was not until later in 1969 that the first standard protocol for the network was established, called at first Host-Host protocol and later the Network Control Program (NCP). These protocols developed by the team of hackers were, at first, restricted to early versions of telnet (remote login to another computer) and ftp (file transfer protocols) (Crocker). Electronic mail, the most common use of the Internet for most of its history, was not implemented until 1971.
Work to the develop the network continued with the support and guidance of ARPA, which Croker characterizes as occasional “redirection.” However, from the beginning of the ARPANet project, the actual creation of the network was the work of an ad hoc group of computer scientists and students from around the United States, soon to be called the called the Network Working Group. Writes Croker:
The initial experiment had been declared an immediate success and the network continued to grow. More and more people started coming to meetings, and the Network Working Group began to take shape. Working Group meetings started to have 50 and 100 people in attendance instead of the half dozen we had had in 1968 and early 1969. We held one meeting in conjunction with the Spring Joint Computer Conference in Atlantic City in 1971. In October 1971 we all convened at MIT for a major protocol “fly-off”. Representatives from each site were on hand, and everyone tried to log in to everyone else’s site. With the exception of one site that was completely down, the matrix was almost completely filled in, and we had reached a major milestone in connectivity. (“RFC 1000”)
For the most part, ARPA allowed the members of the Network Working Group (NWG) to organize themselves, determining what sorts of initiatives should be taken in what areas. With the creation of electronic mail protocols between 1971 and 1973, and distributed conferencing some time after that, members of the NWG could communicate over the very network they were developing (Zitner A-96).
The initial packet switching technology, though allowing decentralized data distribution and sharing among computers running different operating systems, did not allow communication of between networks using different protocols. The next technical step in the network’s development was 1972, when the First International Conference on Computer Communications was held in Washington, D.C. By then, there were forty hosts on the network, and representatives from several countries attended (Hardy). The principle item of discussion was the creation of a new standard network protocol, first proposed by Robert Kahn, which would allow networks outside ARPANet to communicate with ARPANet members and each other. A successor to the NWG, the InterNetwork Working Group (INWG), was created with Vinton Cerf as its first chair, with the goal of creating a suite of network protocols which would allow independent, autonomous networks to communicate with each other (Hardy).
In 1974, Cerf and Kahn proposed a solution to the internetworking challenge: implement a standard suite of internetworking protocols among a series of gateways which connected networks (Cerf, “RFC 1160”). This theoretical basis for internetworking was made practical by an ARPA-sponsored research program, the result of which was the TCP/IP Internet Protocol Suite, commonly called TCP/IP after its two principle protocols, Transmission Control Protocol (TCP) and Internet Protocol (IP) (Comer, Internetworking 6). TCP/IP took its current form between 1977 and 1979.
The internetworking research program was very much a group effort. In its early stages only a few researchers worked to develop and test versions of the internet protocols, but over time the size of this activity increased until, in 1979, it was necessary to form an informal committee to guide the technical evolution of the protocol suite. This group was called the Internet Configuration Control Board (ICCB), and included researchers from all over the United States (Cerf, “RCF 1160”).
Prior to the implementation of TCP/IP, ARPANet was a large, but closed, network. All the connected sites were ARPANet sites: universities, military bases, government offices and research sites. TCP/IP transformed the ARPANet into an internet, allowing ARPANet machines to communicate with computers on other networks such as Bitnet and the Computer Science Network (CSNET), established in 1979 (Comer, Internet 64). True internetworking began in 1980, with ARPANet becoming the backbone network to what at that point was called the APRA Internet (Hardy). In 1983, the military network, MILNET, split from ARPANet, and TCP/IP became the official government standard for long-haul networks.
Although TCP/IP is a robust and in many ways a unique set of protocols, it became a standard in large part due to ARPA’s distribution of the protocol at a low cost, and the agency’s funding of its implementation as part of the most popular mainframe computer operating language, Berkeley Unix, just as many facilities were buying or upgrading their computers (Comer Internetworking 7). Although it may be a bit of a generalization, this process seems to exemplify something of the mediation which took place between conflicting institutional and individual goals; while computer scientists attempted to facilitate the creation of what Cerf has called a “highly robust technology for supporting military command and control,” ARPA adopted something of the hacker ethic in its acceptance of a decentralized structure and its virtually free distribution of protocol specifications in order to make TCP/IP ubiquitous (qtd. in Hafner and Cisler 154; Comer 23).
In many ways, the administrative decentralization of the network preceded its true technological decentralization. While packet switching technology avoided the client-server relationships of other networks, ARPA also allowed the developers of the network to organize themselves. One of the principle tools for this were Request for Comments, or RFCs, a series of numbered electronic documents which formed the basis for determining network standards (Croker). These documents served as an early distributed conference focusing on the development of ARPANet; in browsing them, one can read of ongoing discussions of network protocols, announcements and minutes of NWG meetings, proposals for new innovations, comments on other’s work, and even informal histories and interviews (Croker). Such writers as John Quarterman, Howard Reingold, and Bruce Sterling might contend that RFCs were the first effort by ARPANet users to build community.
Quarterman argues that while ARPANet was established for particular institutional needs, users of the network modified existing technologies to create tools which were used at first for communication, and then to create community (48). As I mentioned earlier, electronic mail was not part of the original 1969 suite of network services. At first glance this may seem odd, as conferencing and electronic mail had been part of mainframe computing from its earliest development in the late-1940s (Hardy). However, the ARPANet was established to facilitate the sharing of computer resources, and it was not until hackers at various ARPANet sites began to modify the original network protocols that a different use for the network emerged. The creation of the electronic mail protocol reflects this; although there is some disagreement as to the origin of email on ARPANet, its present form is based in large part on the standard header format borrowed from the TENEX (Digital PDP-10) operating system, which was used in the file transfer protocol of the then “orthodox” ARPANet protocol suite (Quarterman 38). Within two years of its creation, ARPANet was being used primarily for communication. Writes Sterling:
ARPANet’s users had warped the computer-sharing network into a dedicated, high-speed, federally subsidized electronic post-office. The main traffic on ARPANet was not long-distance computing. Instead, it was news and personal messages. Researchers were using ARPANet to collaborate on projects, to trade notes on work, and eventually, to downright gossip and schmooze. People had their own personal user accounts on the ARPANet computers, and their own personal addresses for electronic mail. Not only were they using ARPANet for person-to-person communication, but they were very enthusiastic about this particular service - far more enthusiastic than they were about long-distance computation. (“History of the Internet”)
The second phase of Internet development, which began roughly around the time of the implementation of the TCP/IP protocols, is characterized by significant growth, and an even greater desire for community-building. During the early-1980s, the principle institutional support for the development of the network shifted from the military to the research community, in the form of the National Science Foundation (NSF). In 1985, the NSF linked its five supercomputer research centres by means of wide area network (WAN) which used TCP/IP protocol, and linked this network to the Internet, thus establishing NSFNet (67).
The goal of the NSF was broader than ARPA’s; very much in keeping with the re-emphasis in this period on American research and development, the foundation wished to extend network access to every science and engineering researcher in the United States(Comer, Internet 73). While the ARPANet Internet backbone had been useful, it was no longer being upgraded to handle higher capacities and levels of use (68). With congressional support, NSF funded co-operative development by a variety of private and public organizations of create two types of networks: a new national backbone which would replace ARPANet and the original NSFNet; and a number of high-speed regional networks. Just as with the development of the first ARPANet, the reason for the creation of this new backbone was resource sharing, but almost immediately, it was used for other purposes. Quarterman indicates that only two percent of NSFNet traffic in the late-1980s was actually devoted to remote login to NSF-supported supercomputers (48).
This phase of the Internet’s development is characterized by a transition from communication to the creation of online communities. Quarterman relates that as early as 1978, hackers had created what was most likely the first true distributed electronic conference, called SF-LOVERS, concerned with science fiction literature and film. The creation of the list was not sanctioned by anyone; it simply used existing technology in the form of modified electronic mail protocols. Because of the distributed nature of the ARPANet administration, SF-LOVERS was difficult to suppress, despite some efforts to do so (Quarterman 48).
Eventually other mailing lists developed, using the Simple Mail Transfer Protocol (SMTP) to send the same sets of messages to a large number of users. Conferencing of this type had a parallel growth under the Unix-to-Unix Copy Protocol (UUCP), which was developing at the same time as ARPANet in the 1970s. The popularity of such lists had prompted a group of hackers, mostly university and high school students at a number of East Coast sites, to attempt to organize a more formal conferencing system. This project, which would eventually become Usenet, was an effort to create a useful community-building tool for the exchange of a variety of information, and as well as a compromise to ARPANet administrators who believed that distributed mailing lists placed an unnecessary burden on the network (Moraes).
The group, which included Tom Truscott and Jim Ellis at Duke University, and Mark Horton and high school student Matt Glickman at Berkeley, created a set of scripts for organizing conference messages at a central location on each host computer which subscribers could access, analogous to looking at a bulletin board (Hardy; Moraes). This system, which was under constant development from 1979 to 1986, became the system of Usenet newsgroups which we use today.
Usenet has its conceptual origins in such computer conferencing systems as Delphi in the early 1970s, borrows its philosophy from ARPANet’s BBOARD utility, and was technically constituted from UUCP and ARPANet mail protocols. By 1988, Usenet had over 400 discussion groups, running under the Network News Transfer Protocol (NNTP), a set of cross-platform standards which had replaced UUCP (Quarterman 45). Today, globally distributed Usenet groups number more than 9000.
The constant mediation between authority and individual needs, central to the development of the Internet, can be seen within the networking community itself. By 1988, a group of system operators at a number of important ARPANet sites had established an administrative body for Usenet, dedicated to providing stable news feeds and electronic mail. This group began to be referred to, with more that a bit of irony, as the “backbone cabal” (Hardy). Typically, Usenet newsgroups are created using a quasi-democratic system in which Usenet users have the opportunity to vote on whether or not a new group should come into existence. In 1987 two groups which dealt with the recreational use of drugs and sexual techniques had been proposed and accepted, but the backbone administrators refused to allow them on their sites. Writes G. Wolffe Woodbury of the event:
But the most profound change to the net occurred when Richard Sexton proposed “rec.sex” (followed closely by rec.drugs) and the group “passed” its "vote" but the Backbone Cabal decreed that they would NOT carry the group or create the group on the “backbone” machines. Almost immediately, the “alt” distribution was set up, using alternative routes that were “separate” from the backbone (and theoretically avoided traversing the ARPANet). Alt.sex, alt.drugs were the first groups created, and the next day, Brian Kantor (sic) issued the newgroup for alt.rock-n-roll (for aesthetic purposes, said he!) Shortly thereafter, (within about 5 months), the Backbone Cabal “officially” abdicated (due to some dissension in the ranks over the control of routing and newgroup guidelines) after installing the “Holey Guidelines” and “Gene Spafford” as the new.group Tsar.
Because the development of the Usenet protocol (NNTP) was a volunteer effort and the technology non-proprietary, any site administrator with enough technical knowledge could write his own scripts and create his own newsgroups, even if their distribution might be limited. In 1988, this is exactly what happened when Brian Reid established the alt hierarchy on his own computer; the alt newsgroups now number in the hundreds and are nearly ubiquitous (Hardy). Although to the reader, Usenet seems to be a single system encompassing thousands of newsgroups, there is in fact a clear division between groups which are under quasi-democratic control, and those groups which any site can create and distribute (Moraes).
If such generalizations can be made, the Internet entered a third phase in its development when the NSF choose three organizations - International Business Machines (IBM), long-distance telephone carrier MCI, and MERIT, a organization which had created an educational infrastructure in Michigan - to build a new Internet backbone in 1987 (Quarterman 68). The backbone was established in 1988, and in 1990, APRANET was taken out of service (Hardy).
As we have seen, each phase of the Internet’s growth has been characterized by a relationship between individuals who shared some or all of what Levy called the hacker ethic, and institutions which funded their creation of the matrix. We have also seen how modification of existing technologies and protocols have been used consistently in both informal co-operation among volunteers and organized research groups (such as the Internet Activities Board) to create new means of communication over the network, and to build community.

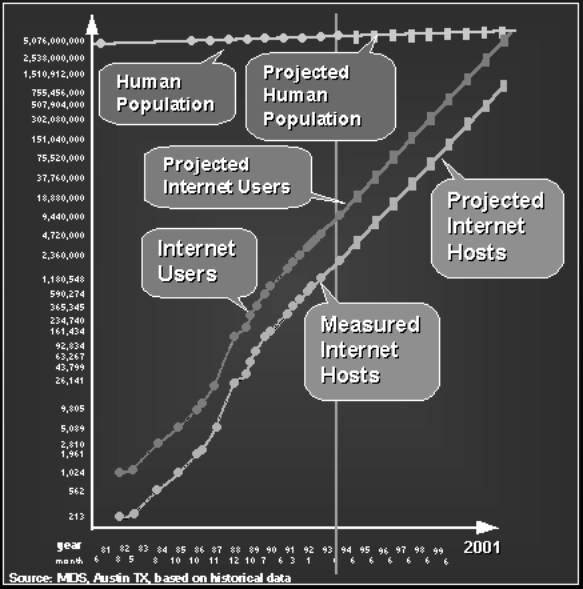
Figure 1: Internet development and projected growth. Information from Quarterman (37) and the Internet Society (“Internet Survey”; “Internet Evolution”).
The third phase of the Internet’s development has been characterized by rapid growth in both users and host computers, as shown in Figure 1 above. In the third quarter of 1994 alone, the number of host computers on the Internet grew an astonishing 21%, the highest increase in four years, and according to Comer, a new computer is being added to the Internet every thirty seconds, with the number of users doubling every ten months (Internet 71). High levels of network traffic have been too much for the old infrastructure funded by the NSF; in 1995, NSFNet will wind down, leaving the management of the main Internet backbone network to a non-profit consortium of businesses and regional networks called the Commercial Internet eXchange Association (CIX) (Wolf). At the same time, friendly, graphical interfaces to the network have been developed, in particular the World Wide Web and Gopher, which require little or no technical expertise to use.
In the past five years, millions of people have been given access to the Internet through commercial providers at both the national and local levels. This new mass of network users require an easy-to-use interface to utilize a variety of bandwidth-intensive services, and are attracted to the utility of the Internet, not necessarily the hacker ideals of co-operative development and free flow of information. This sudden and profound shift in the matrix’s user base, from researchers, academnics, students and hackers to a large number of computer-savvy consumers and business people, is transforming the core dynamic of the Internet to one of a relationship between consumer and service provider. The Internet is being put to uses which could not even have been imagined three years ago, let alone at the network’s creation in 1969, and the co-operative, do-it-yourself philosophies of the hacker which have been embodied in the very technology of the net are becoming a smaller and smaller part of the Internet development process. As the decade progresses, the Internet will increasingly reflect this new dynamic, and be irrevocably transformed.
As we discuss future broadband technologies, we must be aware of the particular processes which constructed the Internet, and to ask critically if they will be repeated in new media as well. Some would contend that they can, believing unproblematically that old protocols and philosophies will simply be transferred to the new infrastructure (Girard). I would argue, however, that the dynamics creating the new "Information Superhighway" are significantly different, and that the emerging infrastructure will bare little relation to the Internet of today either in terms of content, control, or cost. In order to deal with this emerging technology, it is important, I think, to begin to move beyond the superficial examinations of technical detail (typified by Comer and Hardy) or the pleasant discourse technological determinism (Reingold and others) toward a broader examination of the Internet as a cultural artifact.
One can only hope that writers such as Quarterman are correct, and that the core narrative of the Internet is, at least in part, that of transforming technological constructs developed to extend government power into devices which increase contact and communication among groups with shared interests. The Infobahn will be built, to a great extent, through a dynamic between client and server. It will be up to us to choose whether we wish to confront the technology as passive consumers, or more actively, if not as hackers, then at least as engaged and concerned citizens of an emerging cyberspace. Ultimately, our choice will be to determine just what sort of technological community we wish to live in. ~ John Stevenson
Appadurai, Arjun. “Disjunction and Difference in Global Cultural Economy.” Public Culture 2.2 (1990): 2-24.
Cerf, V. “The Network Activities Board.” Network Working Group Request for Comments 1160, August 1990. Electronically distributed, ftp://nri.reston.va.us/
Comer, Douglas E. Internetworking with TCP/IP. Englewood Cliffs: Prentice Hall, 1991.
----. The Internet Book: Everything You Need to Know About Computer Networking and How the Internet Works. Englewood Cliffs: Prentice Hall, 1993.
Crocker, Stephen D. “The Origins of RFCs.” Network Working Group Request for Comments 1000, August 1987. Electronically distributed, ftp://nri.reston.va.us/
Electronic Frontier Foundation. EFF's Guide to the Internet, v.2.21. 1994. Electronically distributed, http://www.eff.org/
Foucault, Michel. “Space, power and knowledge.” The Cultural Studies Reader. Ed. Simon During. London: Routledge, 1993. 161-169.
Girard, Bruce. Personal interview. 1 Nov. 1994.
Hafner, Katie, and Steve Cisler. “The Creators: Twenty-five years ago, they brought the Internet to life.” WIRED 2.12 (1994): 152-154.
Hardy, Henry Edward. The History of the Net. Unpublished Master’s thesis. Allendale: Grand Valley State University, 1993. Electronically distributed, gopher://umcc.umich.edu/
Hauben, Michael. Letter to Association for History & Computing re. RFC1000 - Questions about the origins of ARPANet Protocols , 21 November 1993.
Hedrick, Charles. “Introduction to the Internet Protocols.” Computer Science Facilities Group, Rutgers Centre for Computers and information Services, 1988. Electronically distributed, ftp://rutgers.edu/
Internet Society. “Frequently Asked Questions: What is the Internet Society?” 2 Apr. 1994. Electronically distributed, gopher://gopher.isoc.org:70/
---. “Internet Evolution.” Chart. 4 Nov. 1994. Electronically distributed, http://www.isoc.org/
---. “Internet Survey Reaches 3.8 Million Internet Host Level; 3rd Quarter 1994 Growth is 21 Percent.” Press release. 4 Nov. 1994. Electronically distributed, http://www.isoc.org/
Krol, E. “The Hitchhikers Guide to the Internet.” Network Working Group Request for Comments 1118, September 1989. Electronically distributed, ftp://rutgers.edu/
Levy, Steven. Hackers: Heroes of the Computer Revolution. New York: Dell Publishing, 1984.
Marine, A. and G. Malkin. “FYI on Questions and Answers: Answers to Commonly asked ‘New Internet User’ Questions.” Network Working Group Request for Comments 1206, February 1991. Electronically distributed, ftp://rutgers.edu/
Moraes, Mark. “USENET Software: History and Sources.” Posting to Usenet newsgroups news.admin.misc, news.announce.newusers, news.software.readers, news.software.b, news.answers. 28 October 1994.
Postel, J. and J. Reynolds. “Official Internet Protocols.” Network Working Group Request for Comments 1011, May 1987. Electronically distributed, ftp://rutgers.edu/
Quarterman, John S. “The Global Matrix of Minds.” Global Networks: Computers and International Communications. Ed. Linda M. Harasim. Cambridge: MIT Press, 1993. 35-56.
Reingold, Howard. “Virtual Communities.” 1992. Electronically distributed, gopher://well.sf.ca.us/
Sterling, Bruce. The Hacker Crackdown. 1993. Electronically distributed, gopher://well.sf.ca.us/
Stevenson, John. The Pocket Guide to the Electronic Frontier. April 1994.Electronically distributed, http://tdg.uoguelph.ca/
Williams, Raymond. Television: Technology and Cultural Form. Fontana/Collins, 1973.
Wolf, Gary. “The End of the Internet?” WIRED 2.11 (1994): 38.
Woodbury, G. Wolffe. “Re: Famous flame wars, examples please?” Posting to Usenet newsgroups alt.folklore.computers, alt.culture.usenet, news.admin.misc. 30 Nov. 1992.
Zitner, Aaron. “A Quiet Leap Forward in Cyberspace.” Boston Sunday Globe, 11 September 1994: A-85, A-96.
Copyright © 1995, 1996, 2001 John Harris Stevenson, tranquileye.com.